
3 Overlooked Embedded Software Elements
Have you ever wondered, while you and your team are busy writing software if the foundation of how embedded software systems are built has changed and left you in the dust? What if while you were busily focusing on getting your product out the...

Learning A New Microcontroller
Contents: Introduction Background For The Beginner The Peripherals System Complexity Support Software Do It Like Phil The Programs GPIO And Timers UART And Timers I2C/SPI PWM ADC Go Crazy And Combine Them All WET And DRY...

Development of the MOS Technology 6502: A Historical Perspective
One ubiquitous microprocessor of the late 1970s and 1980s was the MOS Technology MCS 6502. I included a section on the development of the 6502 in Part 2 of Supply Chain Games, and have posted it as an excerpt here, as I believe it is deserving...

Supply Chain Games: What Have We Learned From the Great Semiconductor Shortage of 2021? (Part 2)
Welcome back! Today we’re going to zoom around again in some odd directions, and give a roundabout introduction to the semiconductor industry, touching on some of the following questions: How do semiconductors get designed and...

Patterns of Thinking: Metaphors in Programming
Several years ago, I once attended an “Object-Oriented Analysis and Design” training. As most such courses go, the instructor began with brushing up on the fundamental OO concepts. When explaining inheritance, the instructor spontaneously...

Reading and Understanding Profitability Metrics from Financial Statements
Whoa! That has got to be the most serious-minded title I’ve ever written. Profitability Metrics from Financial Statements, indeed. I’m still writing Part 2 of my Supply Chain Games article, and I was about to mention something about...
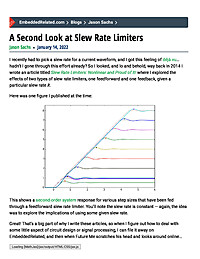
A Second Look at Slew Rate Limiters
I recently had to pick a slew rate for a current waveform, and I got this feeling of déjà vu… hadn’t I gone through this effort already? So I looked, and lo and behold, way back in 2014 I wrote an article titled Slew Rate...

Supply Chain Games: What Have We Learned From the Great Semiconductor Shortage of 2021? (Part 1)
So by now I’m sure you’ve heard about the semiconductor shortage of 2021. For a few complicated reasons, demand is greater than supply, and not everybody who wants to buy integrated circuits can do so. Today we’re going to try...

Review: Modern Software Engineering
This is actually a review of 3 books by Dave Farley, because they really form a set: Modern Software Engineering: Doing What Works to Build Better Software Faster (just released for 2022, 224 pages) Continuous Delivery: Reliable...

VolksEEG: Rust Development On Adafruit nRF52840 Feather Express
Contents: Introduction Setup Hardware Workstation Software Checks USB Device Minicom JLinkExe FTHR840BOOT Contents OpenOCD VolksEEG/eeg-device-firmware PR "Merging initial implementation of the PC communications...

Basler pylon on Raspberry Pi with Yocto
Camera vendors are increasing offering Yocto layers to simplify the integration of drivers and the creation of cross-compilation environments. This article demonstrates how Yocto can be used to integrate Basler pylon into a Raspberry Pi Linux...

Important Programming Concepts (Even on Embedded Systems) Part VI : Abstraction
Earlier articles: Part I: Idempotence Part II: Immutability Part III: Volatility Part IV: Singletons Part V: State Machines We have come to the last part of the Important Programming Concepts series, on abstraction. I thought I might...

Supply Chain Games: What Have We Learned From the Great Semiconductor Shortage of 2021? (Part 3)
Hello again! Today we’re going to take a closer look at Moore’s Law, semiconductor foundries, and semiconductor economics — and a game that explores the effect of changing economics on the supply chain. We’ll try to...

Skills For Embedded Systems Software Developers
Contents: Introduction Do I Need To Be An Expert In Everything? How Much Time Do I need? Do I need A College Degree? Why Is The List So Big? Do I Really Need All These Things? The Skills Software Hardware Software Development...

Learning A New Microcontroller
Contents: Introduction Background For The Beginner The Peripherals System Complexity Support Software Do It Like Phil The Programs GPIO And Timers UART And Timers I2C/SPI PWM ADC Go Crazy And Combine Them All WET And DRY...

Supply Chain Games: What Have We Learned From the Great Semiconductor Shortage of 2021? (Part 2)
Welcome back! Today we’re going to zoom around again in some odd directions, and give a roundabout introduction to the semiconductor industry, touching on some of the following questions: How do semiconductors get designed and...

Working With ESP-C3-32S-Kit Dev Board
Introduction The ESP-C3-32S-Kit is a small dev board made by Ai.Thinker, containing an ESP-C3-32S SoC module, supporting WiFi and BLE: Development for the board uses the Espressif IoT Development Framework...

Absolute Beginner's Guide To Getting Started With Raspberry Pi
The Raspberry Pi is a great little computer for learning programming in general, as well as embedded systems. It runs a version of the Linux OS (Operating System) called Raspberry Pi OS (formerly called Raspbian, so you'll see that name a lot,...

Ten Little Algorithms, Part 5: Quadratic Extremum Interpolation and Chandrupatla's Method
Today we will be drifting back into the topic of numerical methods, and look at an algorithm that takes in a series of discretely-sampled data points, and estimates the maximum value of the waveform they were sampled from.

The Other Kind of Bypass Capacitor
There’s a type of bypass capacitor I’d like to talk about today. It’s not the usual power supply bypass capacitor, aka decoupling capacitor, which is used to provide local charge storage to an integrated circuit, so that the...



















