
Driving I2C-Bus Signals Over Twisted Pair Cables with PCA9605
The availability of powerful I2C buffers that drive their I/Os on both sides to a nominal ground or ‘zero offset’ logic level allows the removal of noise introduced into one section of a larger bus system. That ‘regeneration’ of clean I2C signals enables building long I2C buses by combining together relatively short bus sections, each say less than 20 meters, using such buffers or multiplexers that contain them. Conventional twisted pair communication cabling with its convenient connectors, and a ‘modular’ I2C system approach, make large system assembly easy. Each drop point or node can be individually selected for bidirectional data communication with the Master just by using normal I2C software addressing. As an example, a system is described for control of LED lighting displays and it is suggested that the power for the LEDs, and the I2C control system, might be economically provided using ‘extra low voltage’ distribution at 48 V using either the control signal cable or similar low cost wiring in a manner similar to that used in ‘Power over the Ethernet’ systems. The simplicity and flexibility of this approach makes it attractive to consider as an alternative to other control systems such as RS-485 or CAN bus.

C++ Tutorial
These tutorials explain the C++ language from its basics up to the newest features of ANSI-C++, including basic concepts such as arrays or classes and advanced concepts such as polymorphism or templates. The tutorial is oriented in a practical way, with working example programs in all sections to start practicing each lesson right away
Arduino Programming Notebook
This notebook serves as a convenient, easy to use programming reference for the command structure and basic syntax of the Arduino microcontroller. To keep it simple, certain exclusions were made that make this a beginner’s reference best used as a secondary source alongside other websites, books, workshops, or classes. This decision has lead to a slight emphasis on using the Arduino for standalone purposes and, for example, excludes the more complex uses of arrays or advanced forms of serial communication.

Introduction to Embedded Systems - A Cyber-Physical Systems Approach
This book strives to identify and introduce the durable intellectual ideas of embedded systems as a technology and as a subject of study. The emphasis is on modeling, design, and analysis of cyber-physical systems, which integrate computing, networking, and physical processes. This book is intended for students at the advanced undergraduate level or the introductory graduate level, and for practicing engineers and computer scientists who wish to understand the engineering principles of embedded systems.
Embedded Systems – Theory and Design Methodology
This book addresses a wide spectrum of research topics on embedded systems, including basic researches, theoretical studies, and practical work.
High Performance Systems, Applications and Projects
This book addresses a wide spectrum of research topics of embedded systems, including parallel computing, communication architecture, application-specific systems, and embedded systems projects.

Lessons in Electric Circuits - Volume III - Semiconductor
This book covers all of the common semiconductor devices and their principles of operation. However, the true value of this reference is in the fact that it provides key circuits and applications where they come in handy. A few of the devices that are covered in this book are Bipolar junction transistors, diodes, JFETs, thyristors, OPAMPs and FETs. This book will be a good reference in your library that has a clear style of explanation.

Embedded Linux Primer
This book brings together indispensable knowledge for building efficient, high-value, Linux-based embedded products: information that has never been assembled in one place before. Drawing on years of experience as an embedded Linux consultant and field application engineer, Christopher Hallinan offers solutions for the specific technical issues you're most likely to face, demonstrates how to build an effective embedded Linux environment, and shows how to use it as productively as possible.

A Guide to Approximations
Most embedded processors don’t know how to compute trig and other complex functions. Programming in C we’re content to call a library routine that does all of the work for us. Unhappily this optimistic approach often fails in real time systems where size, speed and accuracy are all important issues. The compiler’s runtime package is a one-size-fits-all proposition. It gives a reasonable trade-off of speed and precision. But every embedded system is different, with different requirements. In some cases it makes sense to write our own approximation routines. Why?

Consistent Overhead Byte Stuffing
Byte stuffing is a process that transforms a sequence of data bytes that may contain ‘illegal’ or ‘reserved’ values into a potentially longer sequence that contains no occurrences of those values. The extra length is referred to in this paper as the overhead of the algorithm. To date, byte stuffing algorithms, such as those used by SLIP [RFC1055], PPP [RFC1662] and AX.25 [ARRL84], have been designed to incur low average overhead but have made little effort to minimize worst case overhead. Some increasingly popular network devices, however, care more about the worst case. For example, the transmission time for ISM-band packet radio transmitters is strictly limited by FCC regulation. To adhere to this regulation, the practice is to set the maximum packet size artificially low so that no packet, even after worst case overhead, can exceed the transmission time limit. This paper presents a new byte stuffing algorithm, called Consistent Overhead Byte Stuffing (COBS), that tightly bounds the worst case overhead. It guarantees in the worst case to add no more than one byte in 254 to any packet. Furthermore, the algorithm is computationally cheap, and its average overhead is very competitive with that of existing algorithms.

An Introduction to programming an Atmega microcontroller
This document an introduction into the programming of an Atmega microcontroller. It is separated into the fi rst part guiding like a tutorial for beginners and a second part which is a reference book to the functions provided in the basis. The examples and explanations provided are neither exhaustive nor complete. The only aim of this document is to lower the burden of getting started. Only a basic knowledge in C is required.
Improving Battery Management System Performance and Cost with Altera FPGAs
The purpose of this white paper is to evaluate improvements to Battery Management System (BMS) performance and cost with Altera® FPGAs. In many high-voltage battery systems, including electric vehicles, grid attached storage and industrial applications, the battery is a significant portion of the system cost, and needs to be carefully managed by a BMS to maximize battery life and to optimize charging and discharging performance. This white paper presents the BMS functional requirements for these applications and outlines existing BMS architectures. Key BMS architectural challenges are discussed and opportunities for Altera devices are identified. For each of these opportunities, the performance and cost of the existing solution are compared with Altera FPGA solutions. Altera devices provide architectural flexibility, scalability, customization, performance improvements, and system cost savings in BMS applications.
Electrical Ground Rules Part 2
Best Practices for Grounding Your Electrical Equipment Examining our use of ground as protection, and how ground fault circuit interrupter devices operate to protect us from severe shock (Part 2 of 3)
What’s a Multicore Microcontroller?
This tutorial answers the question “What’s a multicore microcontroller?”
New Life for Embedded Systems in the Internet of Things
The Internet of Things (IoT) is no longer a fanciful vision. It is very much with us, in everything from factory automation to on-demand entertainment. Yet by most accounts, the full potential of interconnected systems and intelligent devices for changing the way we work and live has barely been tapped. Up until now, IoT software solutions have largely had to be built from scratch with a high degree of customization to specific requirements, which has driven up the cost and complexity of development and deterred many prospective entrants to the market. What have been missing are developer tools that alleviate the costs associated with building the foundational infrastructure—the “plumbing” of their solutions—so they can focus on optimizing the core functionality and bring solutions to market more quickly with less cost. Wind River® is addressing these challenges with new solutions that have the potential to expand the market for IoT by reducing the cost and complexity of development. This document outlines the challenges that IoT poses for developers, and how Wind River solutions can help overcome them.

Guide to designing a device incorporating MEMS-based pico projection
Over the last few years, millions of products incorporating pico projection have shipped, and developers are innovating new applications for this rapidly growing display category. Ideal applications for pico projection include near eye display, interactive digital signage, head mounted display, ultra short throw (UST) TV, standalone portable projectors and embedded projection in smartphones, tablets and laptops. New uses continue to emerge; for example, you might be able imagine a design for a thermostat using a display powered by gesture recognition or interactive touch.
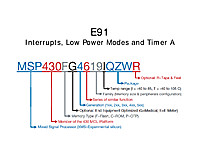
Interrupts, Low Power Modes and Timer A
This document contains a lot of what you need to know to get the most out of the MSP430. The MSP430 line is renowned for it's low power usage, and to really utilize it well you have to architect your software to be an interrupt driven device that utilizes the low power modes.
Reed-Solomon Error Correction
[Best paper on Reed-Solomon error correction I have ever read -- and it's from the BBC!] Reed-Solomon error correction has several applications in broadcasting,in particular forming part of the specification for the ETSI digital terrestrial television standard, known as DVB-T. Hardware implementations of coders and decoders for Reed-Solomon error correction are complicated and require some knowledge of the theory of Galois fields on which they are based. This note describes the underlying mathematics and the algorithms used for coding and decoding,with particular emphasis on their realisation in logic circuits. Worked examples are provided to illustrate the processes involved.

Red Hat Linux - The Complete Reference
This book identifies seven major Linux topics: basic setup, environments and applications, the Internet, servers, administration, and network administration. These topics are integrated into the different ways Red Hat presents its distribution: as a desktop workstation, network workstation, server, and development platform
Debugging Serial Buses in Embedded System Designs
Many embedded system designs utilize serial buses such as I2C, SPI , USB, RS-232/422/485/UART, CAN, LIN, FlexRay and I2S/LJ/RJ/TDM. Learn how to quickly and efficiently debug today’s serial buses with the powerful trigger, decode, and search capabilities of the MSO/DPO Series.



















